I revisited this topic after more then a year to see if anything improved on OCIS or Authelia side.
I made some progress, but still not there yet.
Help me out a bit please.
I run OCIS in docker in a stack with a Nats instance as follows:
version: "3.9"
services:
nodes:
image: owncloud/ocis:7.0
hostname: ocis-{{.Task.Slot}}
ports:
- 9200:9200
networks:
- bana_global
entrypoint:
- /bin/sh
command: ["-c", "if [ \"$OCIS_REPLICA\" = \"1\" ]; then ocis init || true; fi; ocis server"]
environment:
TZ: "Europe/Budapest"
PUID: "1000"
PGID: "1000"
DEMO_USERS: "false"
OCIS_INSECURE: "true"
PROXY_TLS: "false"
PROXY_HTTP_ADDR: 0.0.0.0:9200
OCIS_URL: "https://ocis.my.domain/"
OCIS_LOG_LEVEL: debug
OCIS_LOG_COLOR: "true"
OCIS_LOG_PRETTY: "true"
STORAGE_USERS_OCIS_ROOT: /ocisdata
STORAGE_USERS_ID_CACHE_STORE: "nats-js-kv"
STORAGE_USERS_ID_CACHE_STORE_NODES: "nats:9233"
OCIS_REPLICA: "{{.Task.Slot}}"
OCIS_OIDC_ISSUER: "https://authelia.my.domain"
WEB_OIDC_CLIENT_ID: ownCloud-web
PROXY_OIDC_REWRITE_WELLKNOWN: "true"
PROXY_OIDC_ACCESS_TOKEN_VERIFY_METHOD: none
volumes:
- user-data:/ocisdata
- ocis-data:/var/lib/ocis
configs:
- source: ocis-config
target: /etc/ocis/ocis.yaml
deploy:
mode: replicated
replicas: 1
placement:
max_replicas_per_node: 1
nats:
image: nats
hostname: nats-1
command: [
"--jetstream",
"--store_dir", "/data",
"--port", "9233",
"--cluster_name", "NATS",
"--http_port", "8222",
"--server_name", "nats-1"
]
volumes:
- nats_data-1:/data
networks:
- bana_global
deploy:
mode: replicated
replicas: 1
placement:
max_replicas_per_node: 1
configs:
ocis-config:
file: ./ocis.yaml
networks:
bana_global:
external: true
volumes:
user-data:
driver_opts:
type: "nfs"
o: "addr=LOCALIP,rw,hard,nfsvers=4.2"
device: ":/share/ocisdata"
ocis-data:
driver: local
driver_opts:
type: ''
o: bind
device: /data3/ocis
nats_data-1:
driver: local
driver_opts:
type: ''
o: bind
device: /data3/nats_data-1
User data on NFS 4.2 (not PosixFS yet… I tried really hard tho) Ocis data and Nats on CephFS
My nginx server block is:
server {
listen 80;
listen [::]:80;
server_name ocis.my.domain;
resolver 127.0.0.11 valid=10s;
resolver_timeout 5s;
location / {
return 301 http://$server_name$request_uri;
}
}
server {
listen 443 ssl proxy_protocol;
listen [::]:443 ssl proxy_protocol;
http2 on;
server_name ocis.my.domain;
resolver 127.0.0.11 valid=30s;
resolver_timeout 30s;
ssl_certificate /etc/letsencrypt/live/my.domain/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/my.domain/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
location / {
resolver 127.0.0.11 valid=30s;
resolver_timeout 30s;
set $upstream_ocis http://ocis_nodes:9200;
proxy_pass $upstream_ocis;
proxy_set_header Host $http_host;
proxy_hide_header Content-Security-Policy;
}
}
Notable here that I had to nuke the CSP headers.
I set up Authelia based on
https://helgeklein.com/blog/authelia-lldap-authentication-sso-user-management-password-reset-for-home-networks/
https://helgeklein.com/blog/owncloud-infinite-scale-with-openid-connect-authentication-for-home-networks/#let%e2%80%99s-encrypt-certificate-via-caddy
https://www.authelia.com/integration/openid-connect/ocis/
Big mistake on the last one. Its suggests that you should generate your own client_id and secret and not use the example one. Took me quite a while to figure out that I specifically have to use those values.
So my current authelia config as follows:
identity_providers:
oidc:
lifespans:
access_token: 30d
refresh_token: 30d
jwks:
- key: {{ secret "/config/secrets/IDENTITY_PROVIDERS_OIDC_JWKS" | mindent 10 "|" | msquote }}
cors:
endpoints:
- authorization
- token
- revocation
- introspection
- userinfo
clients:
- client_id: ownCloud-web
client_name: 'ownCloud Infinite Scale'
public: true
redirect_uris:
- 'https://ocis.my.domain/'
- 'https://ocis.my.domain/oidc-callback.html'
- 'https://ocis.my.domain/oidc-silent-redirect.html'
- client_id: xdXOt13JKxym1B1QcEncf2XDkLAexMBFwiT9j6EfhhHFJhs2KM9jbjTmf8JBXE69
client_name: ownCloud desktop client
# Well-known secret as plaintext
client_secret: 'UBntmLjC2yYCeHwsyj73Uwo9TAaecAetRwMw0xYcvNL9yRdLSUi0hUAHfvCHFeFh'
# Well-known secret hashed
# client_secret: '$pbkdf2-sha512$310000$.z/6sV7qQSx1.5zPetVVCQ$JIEPOTFTSokJjDNVhlMLq7tYnHd/E17wSHW.GYXQA0QjfTPqTosyRr7qSHxSiPmXympfTbGF6FmnnX9on.uQng'
scopes:
- openid
- groups
- profile
- email
- offline_access
redirect_uris:
- http://127.0.0.1
- http://localhost
allow_multiple_auth_methods: true
grant_types:
- refresh_token
- authorization_code
response_types:
- code
- client_id: e4rAsNUSIUs0lF4nbv9FmCeUkTlV9GdgTLDH1b5uie7syb90SzEVrbN7HIpmWJeD
client_name: ownCloud Android app
# Well-known secret as plaintext
client_secret: 'dInFYGV33xKzhbRmpqQltYNdfLdJIfJ9L5ISoKhNoT9qZftpdWSP71VrpGR9pmoD'
# Well-known secret hashed
# client_secret: '$pbkdf2-sha512$310000$Grnc1pW0blLl.2B1aEfEvg$JWW3s83SXkgSvoykJ5yD4i11gfrxBOEEGrKXjbyAh.PmVc14FDwSAzxVn7JFXjvO0B0V2RxFsrUT4RZoBK93ug'
scopes:
- openid
- groups
- profile
- email
- offline_access
redirect_uris:
- oc://android.owncloud.com
allow_multiple_auth_methods: true
grant_types:
- refresh_token
- authorization_code
response_types:
- code
- client_id: mxd5OQDk6es5LzOzRvidJNfXLUZS2oN3oUFeXPP8LpPrhx3UroJFduGEYIBOxkY1
client_name: ownCloud iOS app
# Well-known secret as plaintext
client_secret: 'KFeFWWEZO9TkisIQzR3fo7hfiMXlOpaqP8CFuTbSHzV1TUuGECglPxpiVKJfOXIx'
# Well-known secret hashed
# client_secret: '$pbkdf2-sha512$310000$O1agtCxk9EGgvVLZBJumVQ$4UmQmefvIe5jQx1iJDN5pFIuu6CG.v.59wK7xCk3KU6pGbtxGrO0OYtQ/m/TPzE1xZnxgO12.ujXN20sCr/LkQ'
scopes:
- openid
- groups
- profile
- email
- offline_access
redirect_uris:
- oc://ios.owncloud.com
- oc.ios://ios.owncloud.com
allow_multiple_auth_methods: true
grant_types:
- refresh_token
- authorization_code
response_types:
- code
Tried both hashed and non hashed secrets.
With this the web-client works and strangely enough the iOS client.
On windows 11 I got the following client with winget:
Package ID: ownCloud.ownCloudDesktop
Manifest: https://github.com/microsoft/winget-pkgs/tree/master/manifests/o/ownCloud/ownCloudDesktop
Version 5.3.1.14018
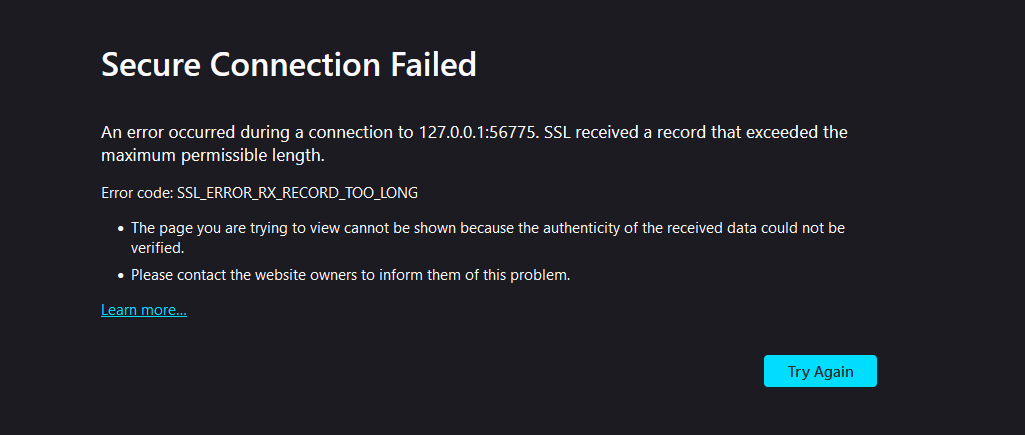
Its redirects me to Authelia in a browser, auth flow goes through then I get this error:
On Android with version 4.4.1 from the PlayStore I get an ‘unknown error’
Connect the phone with adb and running adb logcat --uid=$(adb shell pm list package --user 0 -U com.owncloud.android | sed 's/.*uid://')
I get
01-04 18:56:51.526 20475 26842 D (GetInstancesViaWebFingerOperation.kt:76): D: Successful WebFinger request: WebFingerResponse(subject=acct:myuser@ocis.my.domain/, links=[LinkItem(rel=http://webfinger.owncloud/rel/server-instance, href=https://ocis.my.domain/)])
01-04 18:56:51.528 20475 26842 D (AuthenticationViewModel.kt:159): D: Instances retrieved from authenticated webfinger: Success(data=[https://ocis.my.domain/])
01-04 18:56:51.530 20475 26842 D (ClientManager.kt:80): D: Creating new client for path: https://ocis.mydomain/. Old client path: https://ocis.my.domain, requiresNewClient: false
01-04 18:56:51.531 20475 26842 D (OwnCloudClient.java:91): D: #59Creating OwnCloudClient
01-04 18:56:51.534 20475 26842 D (OwnCloudClient.java:129): D: Executing in request with id 6998ffc7-d50a-402b-a4fd-bb5e44a14039
01-04 18:56:51.564 20475 26842 D TrafficStats: tagSocket(120) with statsTag=0xffffffff, statsUid=-1
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): E: Could not get actuall (or redirected) base URL from base url (/).
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at.bitfire.dav4jvm.exception.DavException: Expected 207 Multi-Status, got 200 OK
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at at.bitfire.dav4jvm.DavResource.assertMultiStatus(DavResource.kt:481)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at at.bitfire.dav4jvm.DavResource.processMultiStatus(DavResource.kt:510)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at at.bitfire.dav4jvm.DavOCResource.propfind(DavOCResource.kt:326)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.http.methods.webdav.PropfindMethod.onDavExecute(PropfindMethod.kt:52)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.http.methods.webdav.DavMethod.onExecute(DavMethod.kt:62)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.http.methods.HttpBaseMethod.execute(HttpBaseMethod.kt:75)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.OwnCloudClient.saveExecuteHttpMethod(OwnCloudClient.java:138)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.OwnCloudClient.executeHttpMethod(OwnCloudClient.java:107)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.resources.files.GetBaseUrlRemoteOperation.run(GetBaseUrlRemoteOperation.kt:52)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.operations.RemoteOperation.runOperation(RemoteOperation.java:264)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.lib.common.operations.RemoteOperation.execute(RemoteOperation.java:229)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource$login$rawBaseUrl$1.invoke(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource$login$rawBaseUrl$1.invoke(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.RemoteOperationHandlerKt.executeRemoteOperation(RemoteOperationHandler.kt:80)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource.login(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource.loginOAuth(OCRemoteAuthenticationDataSource.kt:40)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.data.authentication.repository.OCAuthenticationRepository.loginOAuth(OCAuthenticationRepository.kt:67)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.domain.authentication.usecases.LoginOAuthAsyncUseCase.run(LoginOAuthAsyncUseCase.kt:37)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.domain.authentication.usecases.LoginOAuthAsyncUseCase.run(LoginOAuthAsyncUseCase.kt:27)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.domain.BaseUseCaseWithResult.invoke(BaseUseCaseWithResult.kt:30)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at com.owncloud.android.presentation.authentication.AuthenticationViewModel$loginOAuth$1.invokeSuspend(AuthenticationViewModel.kt:169)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlin.coroutines.jvm.internal.BaseContinuationImpl.resumeWith(ContinuationImpl.kt:33)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.DispatchedTask.run(DispatchedTask.kt:106)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.internal.LimitedDispatcher.run(LimitedDispatcher.kt:42)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.scheduling.TaskImpl.run(Tasks.kt:95)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.scheduling.CoroutineScheduler.runSafely(CoroutineScheduler.kt:570)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.executeTask(CoroutineScheduler.kt:750)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.runWorker(CoroutineScheduler.kt:677)
01-04 18:56:51.648 20475 26842 D (GetBaseUrlRemoteOperation.kt:64): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.run(CoroutineScheduler.kt:664)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): E: ---------------------------------
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): Create RemoteOperationResult from exception.
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): Message: DavException: Expected 207 Multi-Status, got 200 OK
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): Stacktrace: at.bitfire.dav4jvm.exception.DavException: Expected 207 Multi-Status, got 200 OK
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at at.bitfire.dav4jvm.DavResource.assertMultiStatus(DavResource.kt:481)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at at.bitfire.dav4jvm.DavResource.processMultiStatus(DavResource.kt:510)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at at.bitfire.dav4jvm.DavOCResource.propfind(DavOCResource.kt:326)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.http.methods.webdav.PropfindMethod.onDavExecute(PropfindMethod.kt:52)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.http.methods.webdav.DavMethod.onExecute(DavMethod.kt:62)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.http.methods.HttpBaseMethod.execute(HttpBaseMethod.kt:75)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.OwnCloudClient.saveExecuteHttpMethod(OwnCloudClient.java:138)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.OwnCloudClient.executeHttpMethod(OwnCloudClient.java:107)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.resources.files.GetBaseUrlRemoteOperation.run(GetBaseUrlRemoteOperation.kt:52)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.operations.RemoteOperation.runOperation(RemoteOperation.java:264)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.lib.common.operations.RemoteOperation.execute(RemoteOperation.java:229)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource$login$rawBaseUrl$1.invoke(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource$login$rawBaseUrl$1.invoke(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.RemoteOperationHandlerKt.executeRemoteOperation(RemoteOperationHandler.kt:80)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource.login(OCRemoteAuthenticationDataSource.kt:51)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.authentication.datasources.implementation.OCRemoteAuthenticationDataSource.loginOAuth(OCRemoteAuthenticationDataSource.kt:40)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.data.authentication.repository.OCAuthenticationRepository.loginOAuth(OCAuthenticationRepository.kt:67)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.domain.authentication.usecases.LoginOAuthAsyncUseCase.run(LoginOAuthAsyncUseCase.kt:37)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.domain.authentication.usecases.LoginOAuthAsyncUseCase.run(LoginOAuthAsyncUseCase.kt:27)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.domain.BaseUseCaseWithResult.invoke(BaseUseCaseWithResult.kt:30)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at com.owncloud.android.presentation.authentication.AuthenticationViewModel$loginOAuth$1.invokeSuspend(AuthenticationViewModel.kt:169)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlin.coroutines.jvm.internal.BaseContinuationImpl.resumeWith(ContinuationImpl.kt:33)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.DispatchedTask.run(DispatchedTask.kt:106)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.internal.LimitedDispatcher.run(LimitedDispatcher.kt:42)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.scheduling.TaskImpl.run(Tasks.kt:95)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.scheduling.CoroutineScheduler.runSafely(CoroutineScheduler.kt:570)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.executeTask(CoroutineScheduler.kt:750)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.runWorker(CoroutineScheduler.kt:677)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): at kotlinx.coroutines.scheduling.CoroutineScheduler$Worker.run(CoroutineScheduler.kt:664)
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120):
01-04 18:56:51.650 20475 26842 D (RemoteOperationResult.java:120): ---------------------------------
What do I still miss? How come, that some of the clients works, some not.
I mean I like complicated things, but holy shit, getting this far took me weeks.