Steps to reproduce
- configuration of OC 10.8 following documentation at OpenID Connect (OIDC) :: ownCloud Documentation
- Current Univention UCS with OIDC provider (Kopano 2.2-konnect-0.33.11-2)
Expected behaviour
Succesful re-direction to IDP
Actual behaviour
Errror msg " OpenIdConnect:Curl error: (60) SSL certificate problem: self signed certificate in certificate chain" upon account creation in OC client 2.8.1 (linux)
Both OC 10.8 and UCS have NO self-signed certs but LE certs instead.
Server configuration
10.8
Web server:
apache 2.4
Database:
mariadb
PHP version:
7.4
What is the desktop Linux you’re running?
Could you check with a 2.9-prerelease AppImage for comparison?
linux-appimage | download.owncloud.com
Please also check certificate chain with SSL Server Test (Powered by Qualys SSL Labs) or similar. (server and IdP)
I will check 2.9
Linux desktop is SUSE Tumbleweed VERSION=“20210801”
SSL Labs: idp has b rating as forward secrecy is not active, owncloud server has the same, but HSTS is active with the recommended time limits (16000 i think)
What does the SSL test say about the cert chain? I didn’t ask about the general rating or other information.
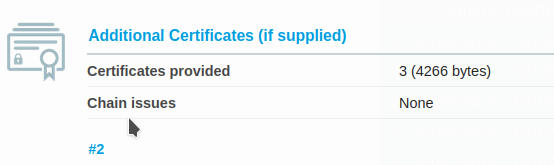
Addendum: the owncloud test server (owncloud2.netzwissen.de) has A+ rating, including HSTS and also “Chain issues: None”
This error msg appears upon connect of the OC client 2.8.1 for OIDC auth. The IDP server has a correct cert chain and LE certs, Nothing is self signed, see attachment of chain. The error message is simply misleading.
Hey,
i think the message is correct:
From what i know curl is a widely used tool and library which is reporting this message. As long as you are not facing a newly uncovered bug in this tool / library it should actually show a correct error message what curl is seeing.
I think there could be at least two reasons for this message:
Your system is too old that it doesn’t know the DST Root CA X3 or ISRG Root X1 certificates which are used to sign the LE certificate.
or
There is a DNS / setup problem and this message is caused because an unexpected server (e.g. a different server or similar) is tried for the connection which has a self signed certificate.
I know that curl is widely used, but this explanation is not really convincing.
The server is idp.netzwissen.de, IP 136.243.85.155 It is a freshly set up (in April 2021) VM with ubuntu 18.04 LTS which has all current patches. On the server there is an Univention UCS 5.0-0 errata59 which is also “up to date”. So, we definitely have no “old software environment” And why should there be a “different server tried for connection”, this makes no sense …
Can someone direct me to location in the code from GitHub - owncloud/client: Desktop Syncing Client for ownCloud with the actual curl request used in this use case? I assume its from /oc-client/src/libsync/creds/oauth.cpp but where is the real curl call string?
Hey,
i don’t think that the desktop client is using curl at all.
I think this message / connection is done on the ownCloud server and the curl installation on the UCS either sees one or more of the certificates in the chain (one of the both previously mentioned) as self signed or sees e.g. idp.netzwissen.de on e.g. 127.0.0.1 and tries to connect to itself but is arriving at a HTTP server having a self signed certificate configured.
ok, I couldnt find any curl calls in the client code. Then it would come form the openid app in the server. Therefore it is -maybe- an issue for Issues · owncloud/openidconnect · GitHub
Hey,
i’m not sure if requires an issue at all as i still think (with my limited knowledge) that this could be a problem in the setup / environment.
But i’m not able to further give additional debugging hints as i have not that much knowledge around this topics and especially UCS. 
Addition:
Maybe you can try to call curl in the docker container (which is running on the UCS) like e.g.:
curl -I https://idp.netzwissen.de
curl -I https://127.0.0.1
and also check what the following in the docker container is returning:
nslookup idp.netzwissen.de
I agree, I am also not shure yet if it is an “issue” of the oidc implementation of OC or a (mis-)config issue in the IDP/UCS. OIDC is great when it works, but not simple to set up…WiIl need some deeper analysis of the idp first …
(info: the virtualisation uses KVM on proxmox, not docker)
haha, yep, its a config issue on the idp, so, its my fault ;-(
root@idp:~# curl -I https://127.0.0.1
curl: (60) SSL: no alternative certificate subject name matches target host name ‘127.0.0.1’
More details here: https://curl.haxx.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.
Hey,
if i’m understanding the output correctly the curl call was done on the IDP server?
But i think the problem might not be on the IDP server (Ubuntu, running on KVM on proxmox) but on the ownCloud server (UCS, running oC in a docker container), that was the reason why i had suggested to run the curl commands in the docker container which is running oC.
The IDP (UCS with kopano for OIDC) runs in another KVM container than the OC server. Both are on the same proxmox host, but they have separate public IPs. The nslookup on the OC server shows:
root@www:~# nslookup idp.netzwissen.de
Server: 127.0.0.53
Address: 127.0.0.53#53
Non-authoritative answer:
Name: idp.netzwissen.de
Address: 136.243.85.155
Hey,
sorry but i misunderstood that you’re running the ownCloud app within the UCS appliance provided by the ownCloud people.
I think the nslookup response looks good, what about the curl call on the oC server for:
curl -I https://idp.netzwissen.de
root@devel:~# curl -I https://idp.netzwissen.de
HTTP/1.1 302 Found
Date: Sat, 07 Aug 2021 14:57:35 GMT
Server: Apache/2.4.38 (Univention)
Location: https://idp.netzwissen.de/univention/
Content-Type: text/html; charset=iso-8859-1
… and this is the oc server log:
{"reqId":"OutMxW7zIfdI7wGnU6jm","level":3,"time":"August 07, 2021 15:24:54","remoteAddr":"127.0.0.1","user":"admin","app":"no app in context","method":"
GET","url":"\/ocs\/v2.php\/apps\/notifications\/api\/v1\/notifications?format=json","message":"User backend OC\\User\\Database is returning home: \/mnt\
/data\/ocdata\/\/admin for user: admin which differs from existing value: \/mnt\/data\/ocdata\/admin"}
{"reqId":"2d3891e3-49fd-46ad-a469-2f18fcdd23d9","level":3,"time":"August 07, 2021 15:28:09","remoteAddr":"127.0.0.1","user":"--","app":"index","method":
"GET","url":"\/index.php\/apps\/openidconnect\/config","message":"Exception: {\"Exception\":\"Jumbojett\\\\OpenIDConnectClientException\",\"Message\":\"
Curl error: (60) SSL certificate problem: self signed certificate in certificate chain\",\"Code\":0,\"Trace\":\"#0 \\\/var\\\/www\\\/owncloud\\\/apps\\\
/openidconnect\\\/lib\\\/Client.php(149): Jumbojett\\\\OpenIDConnectClient->fetchURL()\\n#1 \\\/var\\\/www\\\/owncloud\\\/apps\\\/openidconnect\\\/lib\\
\/Client.php(97): OCA\\\\OpenIdConnect\\\\Client->fetchURL()\\n#2 \\\/var\\\/www\\\/owncloud\\\/apps\\\/openidconnect\\\/lib\\\/Controller\\\/LoginFlowC
ontroller.php(102): OCA\\\\OpenIdConnect\\\\Client->getWellKnownConfig()\\n#3 \\\/var\\\/www\\\/owncloud\\\/lib\\\/private\\\/AppFramework\\\/Http\\\/Di
spatcher.php(170): OCA\\\\OpenIdConnect\\\\Controller\\\\LoginFlowController->config()\\n#4 \\\/var\\\/www\\\/owncloud\\\/lib\\\/private\\\/AppFramework
\\\/Http\\\/Dispatcher.php(89): OC\\\\AppFramework\\\\Http\\\\Dispatcher->executeController()\\n#5 \\\/var\\\/www\\\/owncloud\\\/lib\\\/private\\\/AppFr
amework\\\/App.php(100): OC\\\\AppFramework\\\\Http\\\\Dispatcher->dispatch()\\n#6 \\\/var\\\/www\\\/owncloud\\\/lib\\\/private\\\/AppFramework\\\/Routi
ng\\\/RouteActionHandler.php(47): OC\\\\AppFramework\\\\App::main()\\n#7 \\\/var\\\/www\\\/owncloud\\\/lib\\\/private\\\/Route\\\/Router.php(343): OC\\\
\AppFramework\\\\Routing\\\\RouteActionHandler->__invoke()\\n#8 \\\/var\\\/www\\\/owncloud\\\/lib\\\/base.php(927): OC\\\\Route\\\\Router->match()\\n#9
\\\/var\\\/www\\\/owncloud\\\/index.php(54): OC::handleRequest()\\n#10 {main}\",\"File\":\"\\\/var\\\/www\\\/owncloud\\\/apps\\\/openidconnect\\\/vendor
\\\/jumbojett\\\/openid-connect-php\\\/src\\\/OpenIDConnectClient.php\",\"Line\":1207}"}
So the error happens on the OC server but I have no idea why.