Hi , i have recently installed owncloud and connected it to LDAP server by port 389 but for port 636 i can not connect , what should i do?
Check with the ldapsearch command that the connection is possible.
Perhaps there is a firewall in the way, or the root CA certificate needs to be added to the trust store of your Linux server.
Either way it should show us an error message that should help us figure out what to do next.
I checked the ldapsearch and got error message ldap_result: Can’t contact LDAP server (-1)
i had been added Root CA to below path and run update-ca-certificates
/usr/local/share/ca-certificates/
should i do anything else? or something is wrong?
Please state the command you are using for the ldapsearch, and how you have configured it in your webUI in the LDAP → Server Tab so we can understand what you are doing exactly.
https://doc.owncloud.com/server/10.6/admin_manual/configuration/user/user_auth_ldap.html#server-tab
This view is what we need as well as your command on the command line.
I ran ldapsearch like this , it worked for port 389
ldapsearch -x -h 172.16.1.1 -p 636 -b “dc=mwm,dc=local” -D “CN=own cloud,OU=Service,OU=IT Admin,DC=mwm,DC=local” -W
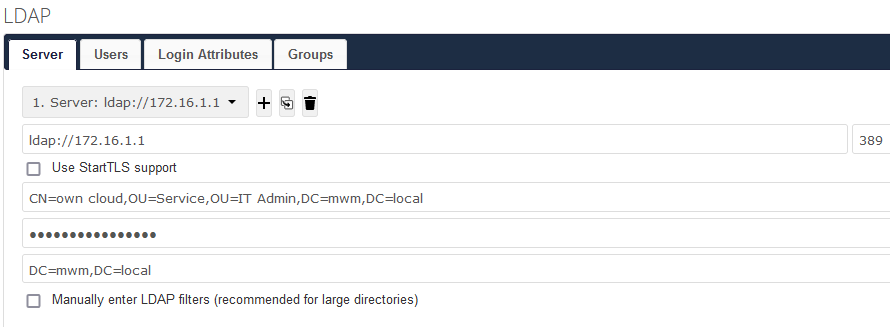
This is the server tab config
Great
Can you now post the non working config with 636?
PS. You should avoid spaces in logins.
Sorry i dont get what you mean i just change the port number . do you want something else? where is your output you want?
You also have to change ldap:// to ldaps:// or it won’t work. I just wanted to check if you configured all correctly in this server tab to make sure you did not forget something 
Hi , i use ldaps:// with pot 636 but i get could not connect to ldap error message
Did that work? Or did you get an error message.
I’d recommend to build an ldapsearch command with port 389 and then just replace protocoll and port in the command.
Can you run ls -al /usr/local/share/ca-certificates/?
I think the certificate file needs to end with .cer for it to be actually added to the trust store.
You need to get the ldapsearch working before you can move on to the ownCloud interface.
If this doesn’t work, it is impossible for it to work in the ownCloud interface.
Check firewalls, try with openssl s_client -connect. We know it’s not a network problem as the same system can be reached on port 389. Perhaps there is still something else missing on the backend side?
Hi i test it i got error , i imported root ca certificate from AD into the server as it’s said in owncloud site this is the output
openssl s_client -connect 172.16.1.1:636
CONNECTED(00000005)
depth=0 CN = DC.mwm.local
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = DC.mwm.local
verify error:num=21:unable to verify the first certificate
verify return:1
Certificate chain
0 s:CN = DC.mwm.local
i:DC = local, DC = mwm, CN = mwm-DC-CA
Server certificate
-----BEGIN CERTIFICATE-----
[Certificate Codes]
-----END CERTIFICATE-----
subject=CN = DC.mwm.local
issuer=DC = local, DC = mwm, CN = mwm-DC-CA
No client certificate CA names sent
Client Certificate Types: RSA sign, DSA sign, ECDSA sign
Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Shared Requested Signature Algorithms: RSA+SHA256:RSA+SHA384:RSA+SHA1:ECDSA+SHA256:ECDSA+SHA384:ECDSA+SHA1:DSA+SHA1:RSA+SHA512:ECDSA+SHA512
Peer signing digest: SHA256
Peer signature type: RSA
Server Temp Key: ECDH, P-384, 384 bits
SSL handshake has read 2023 bytes and written 482 bytes
Verification error: unable to verify the first certificate
New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: 0722000024FF9A62DC0F2B7F4E8788D20413E82EDE6B22431837838996AF1E28
Session-ID-ctx:
Master-Key:
Master-key value
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1623724148
Timeout : 7200 (sec)
Verify return code: 21 (unable to verify the first certificate)
Extended master secret: yes
As you see the below error is shown
CONNECTED(00000005)
depth=0 CN = DC.mwm.local
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = DC.mwm.local
verify error:num=21:unable to verify the first certificate
verify return:1
I was asking for this before as well. Please have a look:
Do you have a self-signed cert or a custom PKI? Did you import the CA certificate or the Server’s certificate. I think you need to import the CA cert.
And if you have a self-signed cert it could be that it doesn’t work at all, not sure.
total 12
drwxr-xr-x 2 root root 4096 Jun 7 07:56 .
drwxr-xr-x 6 root root 4096 Aug 7 2020 …
-rw------- 1 root root 1224 Jun 7 07:56 CA-DER.crt
I have AD and export CA root certificate .
in owncloud site ldap-configuration section says as below
LDAPS encrypts the connection between your LDAP server and ownCloud via SSL/TLS.
First you need the Windows Server CA certificate in the pem format with .crt suffix Import the certificate to /usr/local/share/ca-certificates/ Execute update-ca-certificates
so i change the cer extension to crt , do i need to change it to cer ?
This topic was automatically closed 90 days after the last reply. New replies are no longer allowed.