Prepare IDP
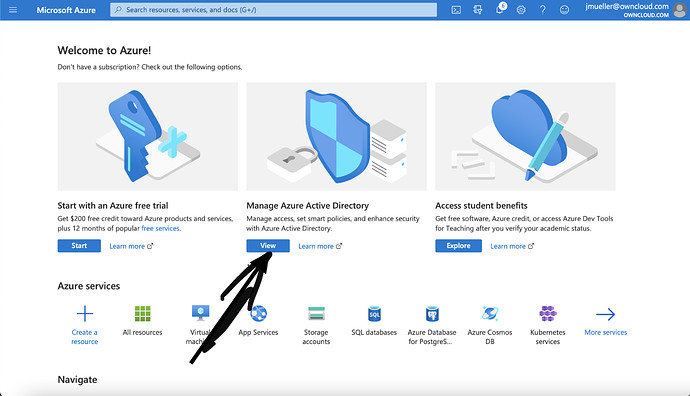
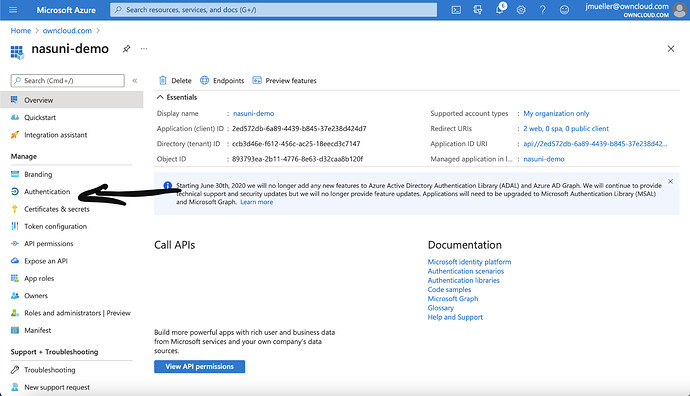
Enter Azure dashboard and Klick on Show on the active directory Panel
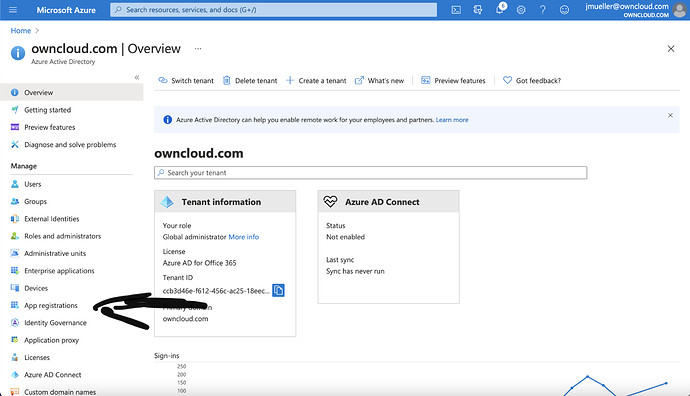
On the Overview Page in Azure AD, click on App-Registration
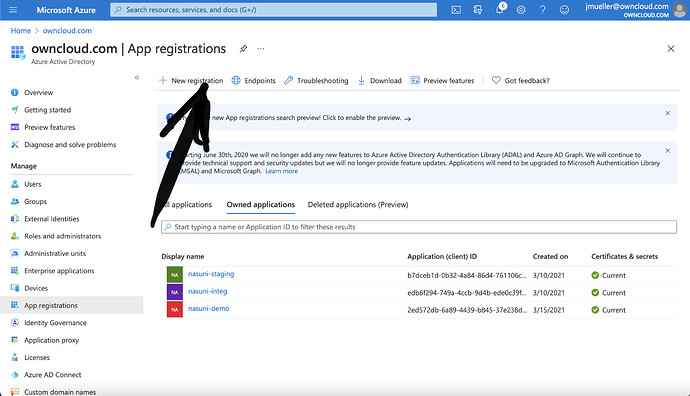
In App-registration, click on „New Registration“
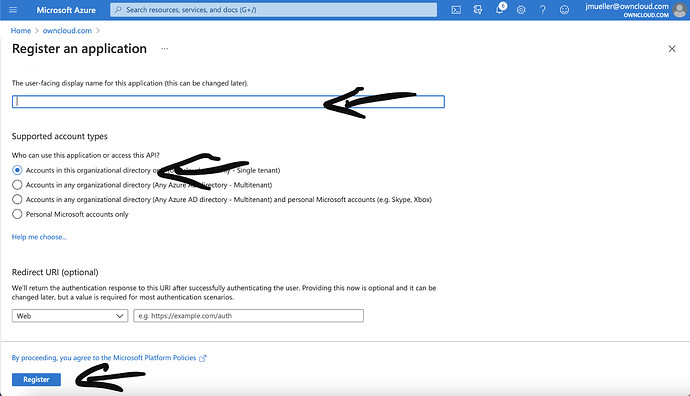
Give the registration a name, e.g. „Nasuni-demo“ in this case. In this case we only select accounts from this organization unit. Finally click on „register“
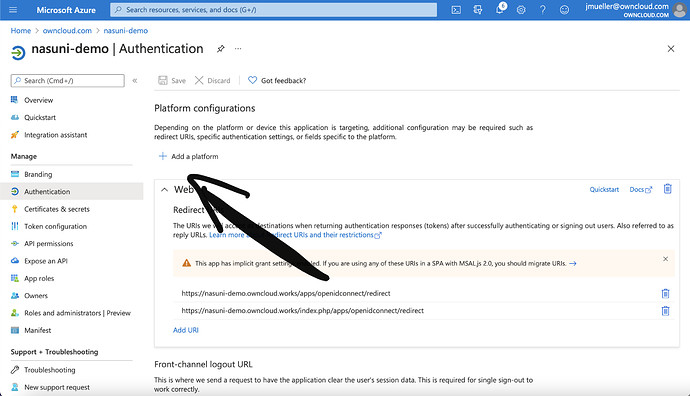
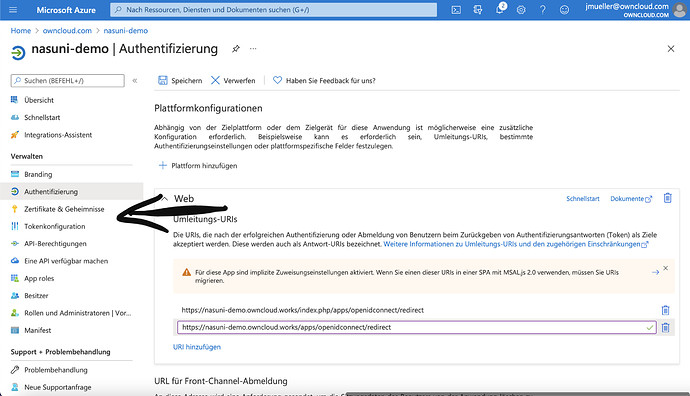
Next, click on „Authentication“
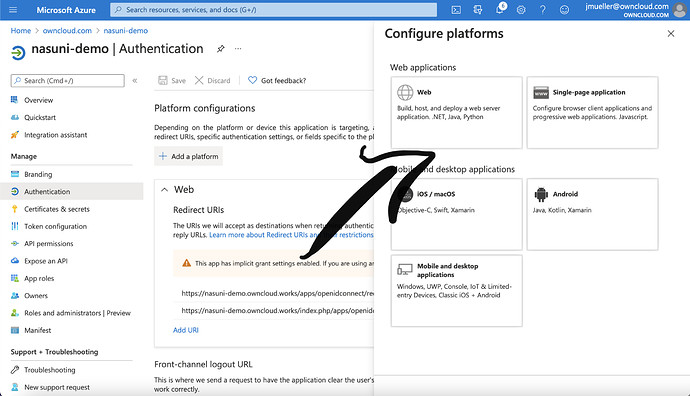
Click on „Add Plattform“
Select „Web“
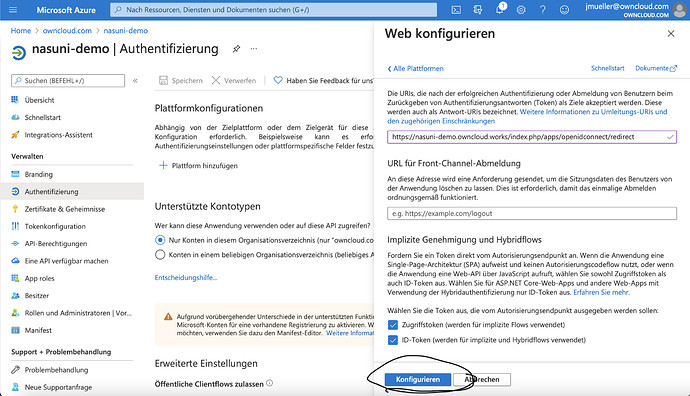
Add the configuration for the platform. According to your setup, you might or might not have to add /index.php/ to the domain. Make sure, the checkboxes for „Access“ and „ID“ Token are ticked. Login domain is not necessary, as oc10 openid app can resolve it by auto discovery.
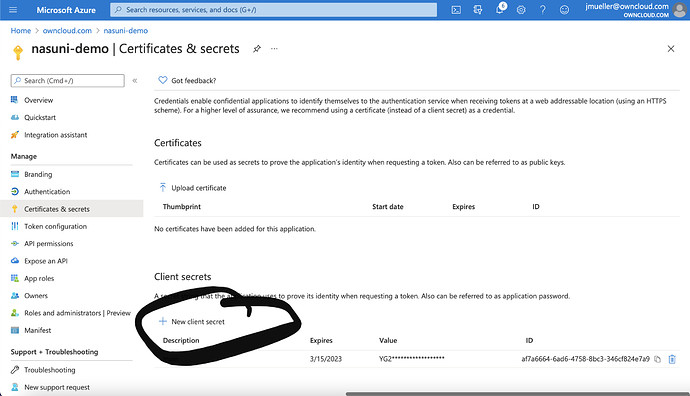
After you clicked on „Configure“, you might want to add the domain without /index.php/ as well. Next, you click on. „Certificate and Secrets“
On that page, you have to scroll to the bottom and click on „New Client Secret“
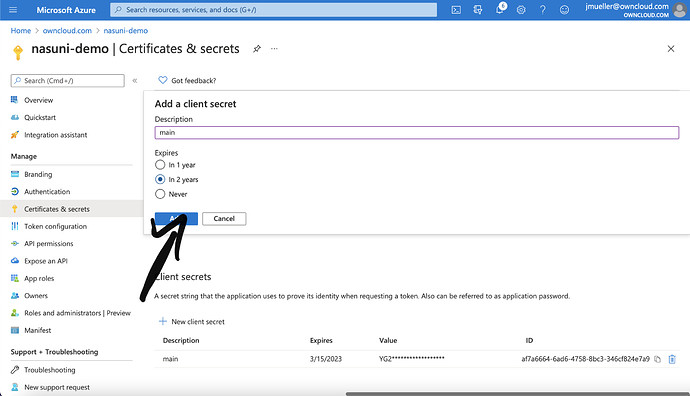
Name it and add a expiry date. Then click on add.
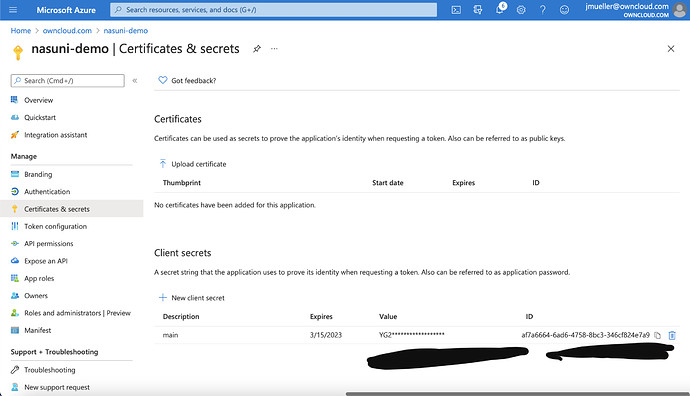
Now the Value and the id have to copied to some place where they are safely stored. They are only visible once!!! After that, click on „Tokenconfiguration“
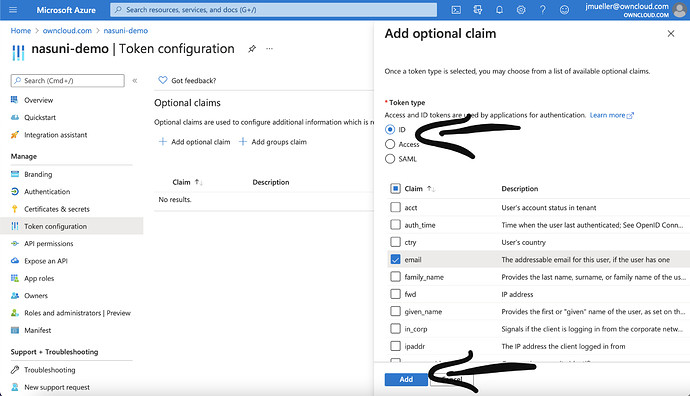
In Token configuration, click on „Add optional claim“
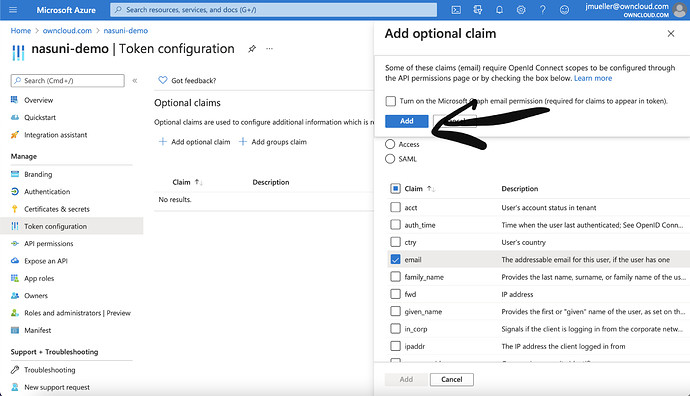
Select ID and in the list that shows up, email and sid and click on „Add“
Select „Turn on the Microsoft Graph Email permission“ and click „Add“
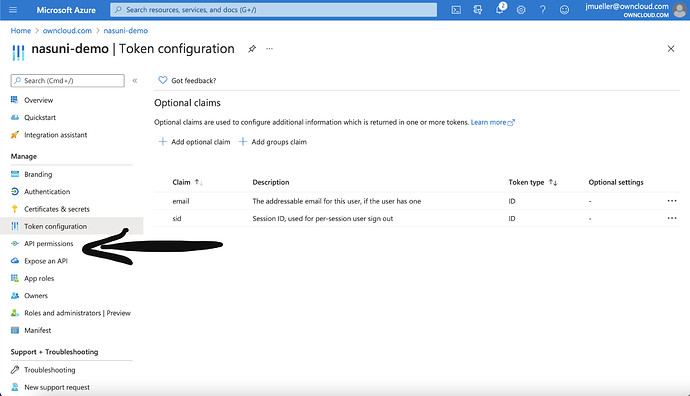
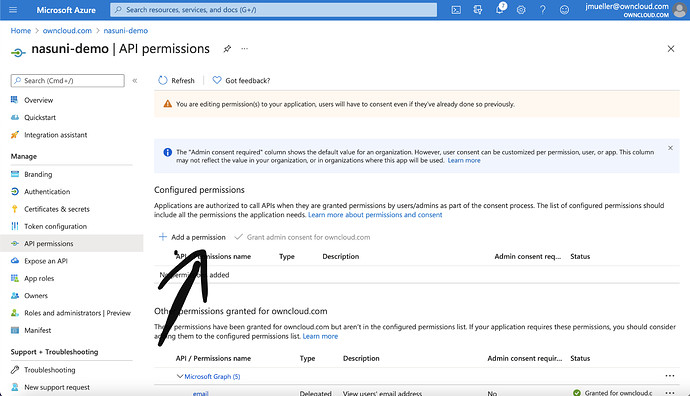
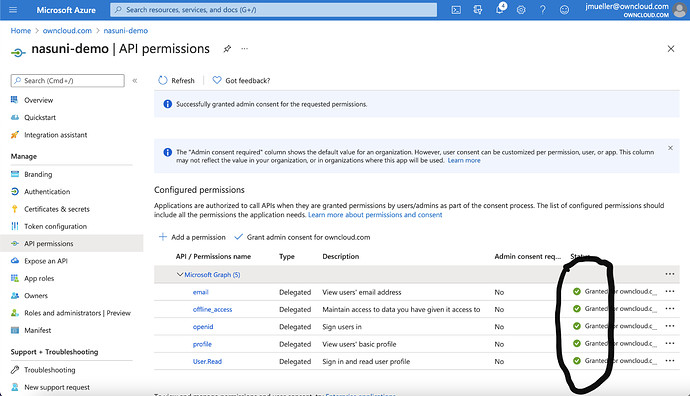
Next click on API permissions
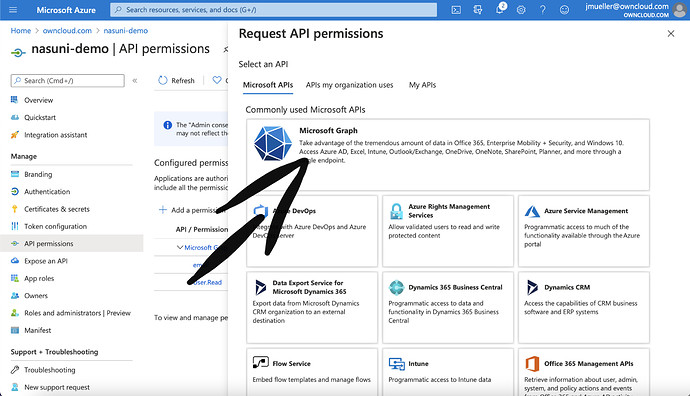
Click on „Add a permission“
Select „Microsoft Graph“
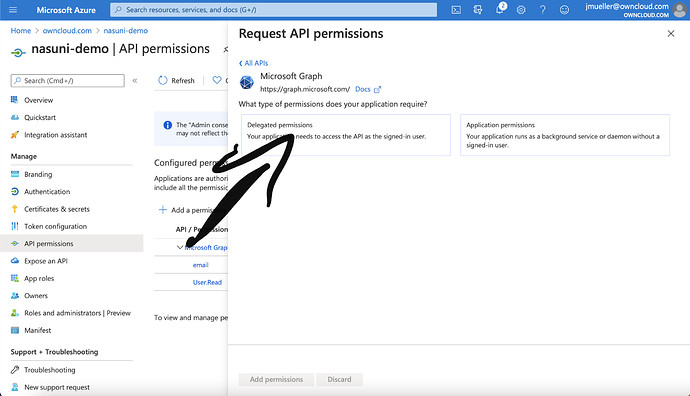
On the next slide, select „Delegated Permissions“
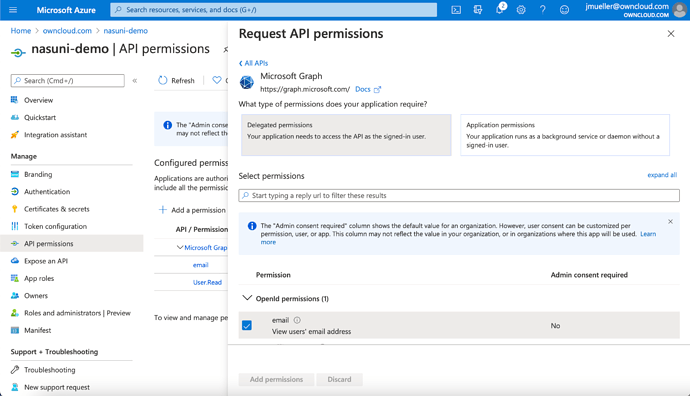
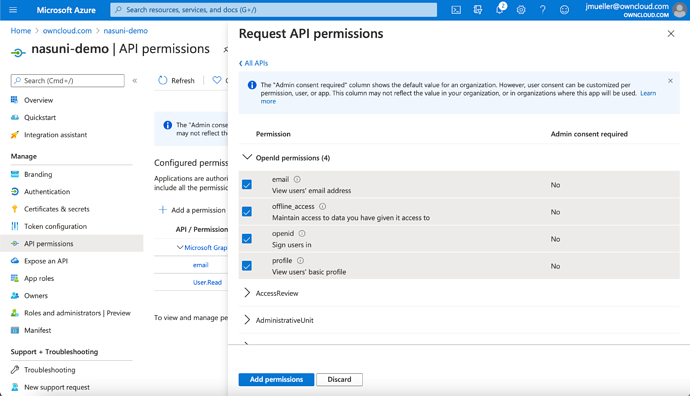
A list with checkboxes will occur.
Select „email“, „offline_access“, „openid“ and „profile“ in the first sublist.
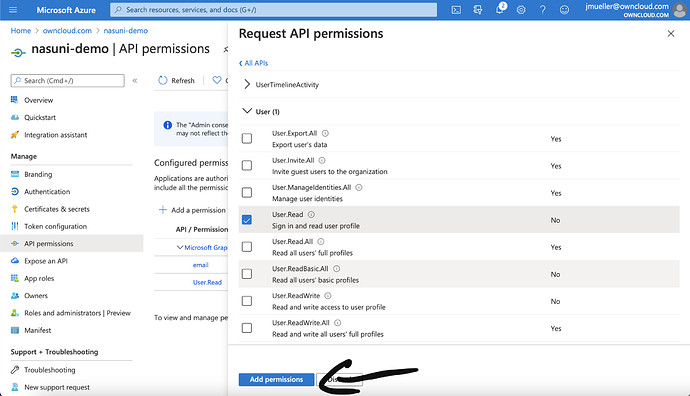
Select „User.Read“ in the last sub list and click on „Add Permissions“
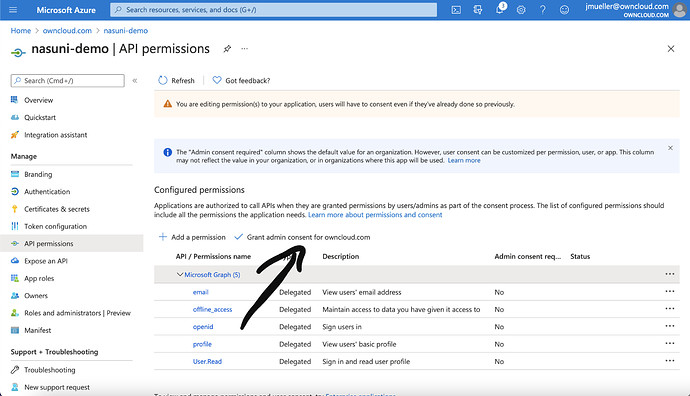
Next, click on „Grant admin consent for “. You have to be global azure admin to have the permission to perform that action.
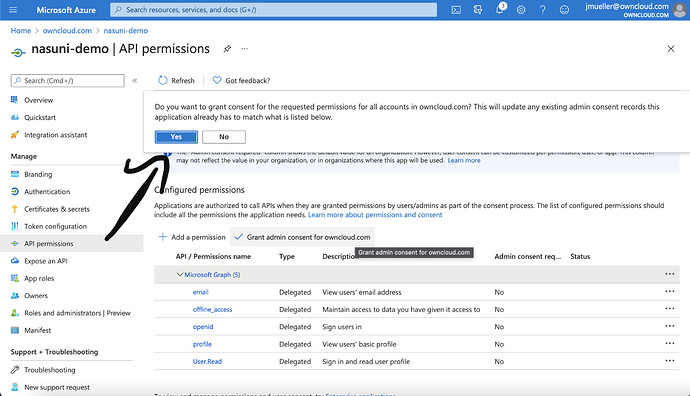
Confirm your will to grant consent… by clicking on „Yes“
Status column will now show green marks like bellow
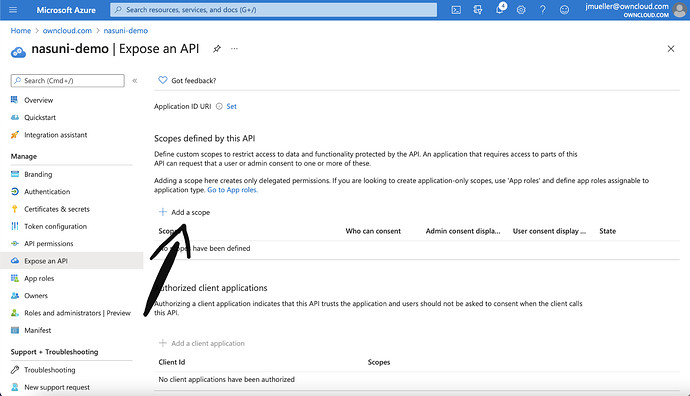
Click on „Expose an API“
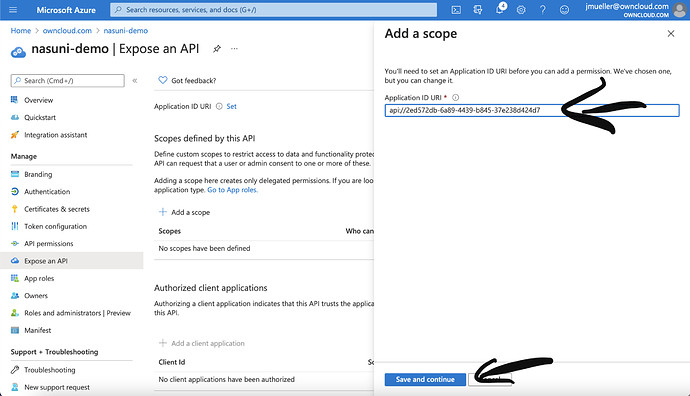
Click on „Add a scope“ and click on „Save and continue“. The hash in the api strip is the application id that you can find on the overview page of the App Registration.
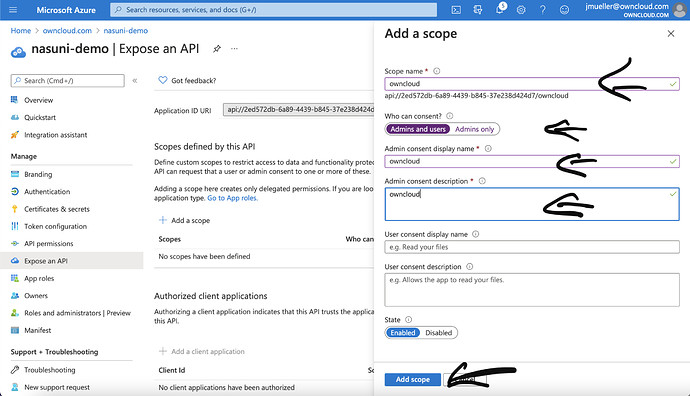
Give the scope a name, display name and description and change „Admins only“ to „Amins and users“. Finally click on „Add scope“.
All steps in Azure for setting up Azure Ad with OpenIDConnect are done at that point. Next is going about how to setup oc10.