Hello, I have configured a custom theme for ownCloud, in the folder apps-external.
/var/www/owncloud/apps-external/theme-custom/core/img
I have replaced all the images in the folder /img to match our custom logos. All ok, except that, when we get notified by the Activity App by email, sometimes the logo-mail.gif is our custom logo (our company logo) but other times, it is the default owncloud logo.
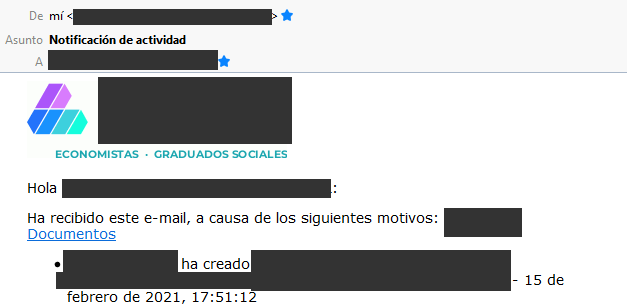
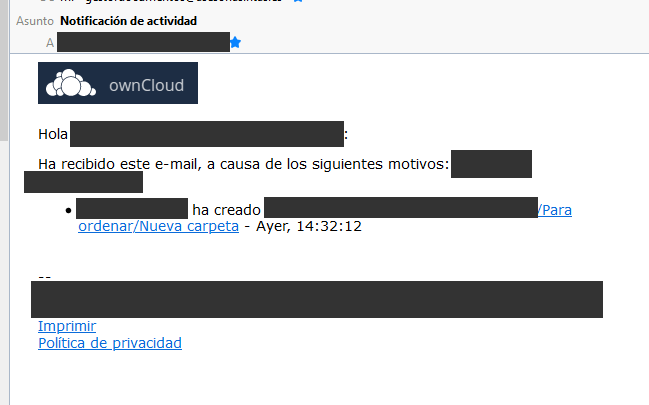
Is there something else I could check?
Steps to reproduce
Expected behaviour
Tell us what should happen
Actual behaviour
Tell us what happens instead
Server configuration
Operating system:
Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0 x86_64)
Web server:
Apache
Database:
mysql Ver 15.1 Distrib 10.5.8-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
PHP version:
PHP 7.4.15 (cli) (built: Feb 14 2021 14:19:46) ( NTS )
Copyright © The PHP Group
Zend Engine v3.4.0, Copyright © Zend Technologies
with Zend OPcache v7.4.15, Copyright ©, by Zend Technologies
ownCloud version: (see ownCloud admin page)
10.6.0.5
Updated from an older ownCloud or fresh install:
Fresh install
Where did you install ownCloud from:
Source
https://download.owncloud.org/community/owncloud-complete-20201216.tar.bz2
Signing status (ownCloud 9.0 and above):
Login as admin user into your ownCloud and access
http://example.com/index.php/settings/integrity/failed
paste the results into https://gist.github.com/ and puth the link here.
The content of config/config.php:
Log in to the web-UI with an administrator account and click on
'admin' -> 'Generate Config Report' -> 'Download ownCloud config report'
This report includes the config.php settings, the list of activated apps
and other details in a well sanitized form.
or
If you have access to your command line run e.g.:
sudo -u www-data php occ config:list system
from within your ownCloud installation folder
{
"system": {
"instanceid": "xxxxxxxxxxxxxxx",
"passwordsalt": "***REMOVED SENSITIVE VALUE***",
"secret": "***REMOVED SENSITIVE VALUE***",
"trusted_domains": [
"localhost",
"xxxxxxxxxxxxxxxxxxxxx"
],
"datadirectory": "\/var\/www\/owncloud\/data",
"overwrite.cli.url": "http:\/\/localhost",
"dbtype": "mysql",
"version": "10.6.0.5",
"dbname": "owncloud",
"dbhost": "localhost",
"dbtableprefix": "oc_",
"mysql.utf8mb4": true,
"dbuser": "***REMOVED SENSITIVE VALUE***",
"dbpassword": "***REMOVED SENSITIVE VALUE***",
"logtimezone": "Europe\/Berlin",
"apps_paths": [
{
"path": "\/var\/www\/owncloud\/apps",
"url": "\/apps",
"writable": false
},
{
"path": "\/var\/www\/owncloud\/apps-external",
"url": "\/apps-external",
"writable": true
}
],
"installed": true,
"memcache.local": "\\OC\\Memcache\\APCu",
"mail_domain": "***REMOVED SENSITIVE VALUE***",
"mail_from_address": "***REMOVED SENSITIVE VALUE***",
"mail_smtpmode": "smtp",
"mail_smtpsecure": "ssl",
"mail_smtpauthtype": "LOGIN",
"mail_smtpauth": 1,
"mail_smtphost": "***REMOVED SENSITIVE VALUE***",
"mail_smtpport": "465",
"mail_smtpname": "***REMOVED SENSITIVE VALUE***",
"mail_smtppassword": "***REMOVED SENSITIVE VALUE***",
"loglevel": 2,
"skeletondirectory": "\/var\/www\/owncloud\/apps-external\/alternative-skeleton",
"integrity.ignore.missing.app.signature": [
"theme-custom"
]
}
}
*ATTENTION:* Do not post your config.php file in public as is. Please use one of the above
methods whenever possible. Both, the generated reports from the web-ui and from occ config:list
consistently remove sensitive data. You still may want to review the report before sending.
If done manually then it is critical for your own privacy to dilligently
remove *all* host names, passwords, usernames, salts and other credentials before posting.
You should assume that attackers find such information and will use them against your systems.
List of activated apps:
Enabled:
- activity: 2.6.0
- comments: 0.3.0
- configreport: 0.2.0
- contacts: 1.5.5
- dav: 0.6.0
- federatedfilesharing: 0.5.0
- files: 1.5.2
- files_antivirus: 0.15.2
- files_external: 0.7.1
- files_mediaviewer: 1.0.4
- files_pdfviewer: 0.11.2
- files_sharing: 0.14.0
- files_texteditor: 2.3.0
- files_trashbin: 0.9.1
- files_versions: 1.3.0
- firstrunwizard: 1.2.0
- market: 0.6.0
- notifications: 0.5.2
- provisioning_api: 0.5.0
- systemtags: 0.3.0
- templateeditor: 0.4.0
- theme-custom: 1.0.0
- updatenotification: 0.2.1
Disabled: - admin_audit
- announcementcenter
- customgroups
- encryption
- enterprise_key
- external
- federation
- files_classifier
- files_external_dropbox
- files_external_ftp
- files_ldap_home
- files_lifecycle
- firewall
- graphapi
- guests
- oauth2
- openidconnect
- password_policy
- ransomware_protection
- sharepoint
- systemtags_management
- theme-enterprise
- user_external
- user_ldap
- user_shibboleth
- windows_network_drive
- wopi
- workflow
If you have access to your command line run e.g.:
sudo -u www-data php occ app:list
from within your ownCloud installation folder.
Are you using external storage, if yes which one: local/smb/sftp/…
no
Are you using encryption: yes/no
no
Are you using an external user-backend, if yes which one: LDAP/ActiveDirectory/Webdav/…
LDAP configuration (delete this part if not used)
With access to your command line run e.g.:
sudo -u www-data php occ ldap:show-config
from within your ownCloud installation folder
Without access to your command line download the data/owncloud.db to your local
computer or access your SQL server remotely and run the select query:
SELECT * FROM `oc_appconfig` WHERE `appid` = 'user_ldap';
Eventually replace sensitive data as the name/IP-address of your LDAP server or groups.
Client configuration
Browser:
Operating system:
Logs
Web server error log
Insert your webserver log here
ownCloud log (data/owncloud.log)
Insert your ownCloud log here
Browser log
Insert your browser log here, this could for example include:
a) The javascript console log
b) The network log
c) ...