Hello, OwnCloudOwners,
I am trying to integrate a new installation of OwnCloud Infinite Scale (Community Edition) with the Janssen Authorization Server, an open-source OIDC provider. The authentication workflow almost succeeds:
- OwnCloud redirects to the SSO sign-in page
- Authentication Credentials are accepted and the requested OIDC scopes for OwnCloud (profile, mail, etc.) are presented to the user for acceptance
- Browser redirects to the OIDC callback page on OwnCloud (
https://oc.[my domain].io/oidc-callback)
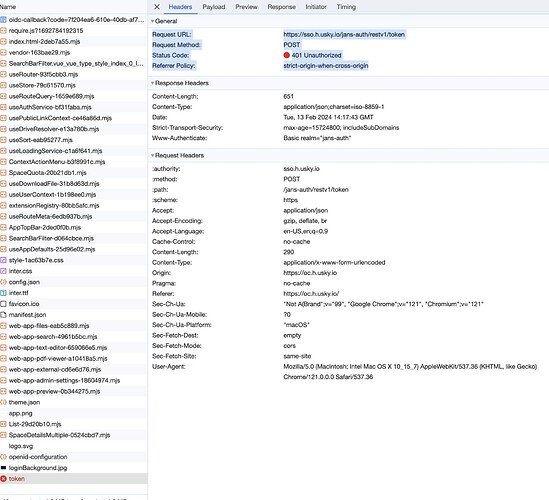
However, when the landing page on OwnCloud attempts to fetch the authorization token via Javascript (a request to https://[my domain]/jans-auth/restv1/token) , a CORS violation occurs and the browser blocks the request.
https://sso.[my domain].io/jans-auth/restv1/token
Request Method:
POST
Status Code:
401 Unauthorized
Referrer Policy:
strict-origin-when-cross-origin
It seems that https://sso.[my domain].io/ needs to be added to the CORS configuration for the OwnCloud frontend. I believe I have done this correctly, but it’s still not working.
I’m deploying OCIS using the Helm charts, and the CORS-related configuration values do seem to be making it into the containers…
❯ kubectl get pod frontend-5d7bfd6fdf-mkc5m -o yaml |\
grep -C 2 OCIS_CORS_ALLOW_ORIGINS
...
- name: OCIS_CORS_ALLOW_ORIGINS
value: '*,https://sso.[my domain].io,https://oc.[my domain].io,https://[my domain].io'
image: owncloud/ocis:4.0.1
also…
❯ kubectl exec frontend-5d7bfd6fdf-mkc5m -- sh -c 'echo $OCIS_CORS_ALLOW_ORIGINS'
*,https://sso.[my domain].io,https://oc.[my domain].io,https://[my domain].io
So the config values have made it at least as far as ENV vars inside the containers. But it seems not all the way to the browser? Seems like I’m missing something obvious.
Any help or tips debugging this will be greatly appreciated.
Thanks in advance,
-b
The OIDC server is hosted at: https://sso.[my domain].io
OCIS is hosted at: https://oc.[my domain].io
Steps to reproduce
- Establish OIDC provider at
https://sso.[my domain].io/ - Deploy OCIS from the Helm charts to
https://oc.[my domain].io, using the following overrides:
externalDomain: oc.[my domain].io
# HTTP settings for oCIS services.
http:
#-- CORS settings for oCIS services.
cors:
#-- allow_origins is a list of origins a cross-domain request can be executed from.
# If the special "*" value is present in the list, all origins will be allowed.
allow_origins: ["*", "https://sso.[my domain].io", "https://oc.[my domain].io", "https://[my domain].io"]
...
features:
basicAuthentication: false
externalUserManagement:
enabled: true
- Attempt to login
Expected behaviour
Browser Javascript requests to https://sso.[my domain].io should be allowed from OwnCloud
Actual behaviour
Browser Javascript requests to https://sso.[my domain].io are blocked by CORS configuration. ![]()
Server configuration
Operating system: Ubuntu 22.04 LTS
Web server: Whatever is packaged into OCIS Community edition 04.0.1 containers
Database: Whatever is packaged into OCIS Community edition 04.0.1 containers
PHP version: I think it’s none? Isn’t OCIS composed of golang microservices?
ownCloud version: 4.0.1
Updated from an older ownCloud or fresh install: fresh install
Where did you install ownCloud from: [Helm charts][1]
The content of config/config.php: Hopefully all CORS-related config is posted above…
List of activated apps: default set for OCIS 4.0.1
Are you using external storage: No
Are you using encryption: no
Are you using an external user-backend: [Janssen Authorization Server][2]
LDAP configuration (delete this part if not used)
ldap:
writeable: true
readOnlyAttributes:
uri: ldaps://ldap.h.[my domain]:1636
certTrusted: true
insecure: false
bindDN: cn=Directory Manager
refintEnabled: false
passwordModifyExOpEnabled: false
useServerUUID: true
user:
schema:
id: inum
idIsOctetString: false
mail: mail
displayName: displayName
userName: uid
userType: ownCloudUserType
baseDN: ou=people,o=jans
scope: sub
substringFilterType: any
objectClass: jansPerson
group:
schema:
id: inum
idIsOctetString: false
mail: mail
displayName: displayName
groupName: inum
member: member
baseDN: ou=groups,o=jans
createBaseDN: ""
scope: sub
filter:
objectClass: jansGrp
using an ldap attribute.
disableUsers:
disableMechanism: attribute
userEnabledAttribute: ownCloudUserEnabled
disabledUsersGroupDN: "cn=DisabledUsersGroup,ou=groups,o=libregraph-idm"
Client configuration
Browser: Chrome, Firefox, Safari (all tested - same results)
Operating system: Windows, Mac, Linux (all tested - same results)