Steps to reproduce
- Make available only via HTTPS via a single port on Apache using a reverse proxy configuration.
- Try to log in or Log out.
Expected behaviour
Should work without trying to redirect to http, without issue.
Actual behaviour
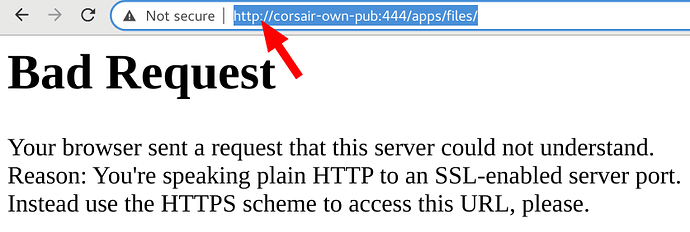
It attempts to access something on http, which results in an exception if http isn’t available. You won’t see this if you have it available on both 443 and 80. In that configuration, it goes to 80, then back to 443 using normal browser semantics. But, if you don’t have it on port 80, or use a port other than 443 for your HTTPS, you get an error. So, if use port 444, I get this:
# Bad Request
Your browser sent a request that this server could not understand.
Reason: You're speaking plain HTTP to an SSL-enabled server port.
Instead use the HTTPS scheme to access this URL, please.
Note that if you force it each time you log in or out to correctly prefix the URL with https again by typing it into the URL, you can continue. You have to do this each time you log in or out.
I have not tried accessing from mobile where you can’t do that, but rely on the client to handle all HTTP communication with a single URL for your remote instance. I only tested using a PC browser.
Server configuration
Operating system:
Linux - Fedora
Web server:
Used your docker compose, then ran reverse proxy to port 8080. This works. However, because I’ll be access multiple instances and other things through a single Apache HTTP server with reverse proxy through a WIFI router using virtual hosting, each one will have only one port and it will use HTTPS.
Reverse proxy through Apache
Database:
MariaDB (your docker compose)
PHP version:
w/e is in your docker compose
ownCloud version: (see ownCloud admin page)
ownCloud 10.6.0 (stable)
Updated from an older ownCloud or fresh install:
Where did you install ownCloud from:
docker compose